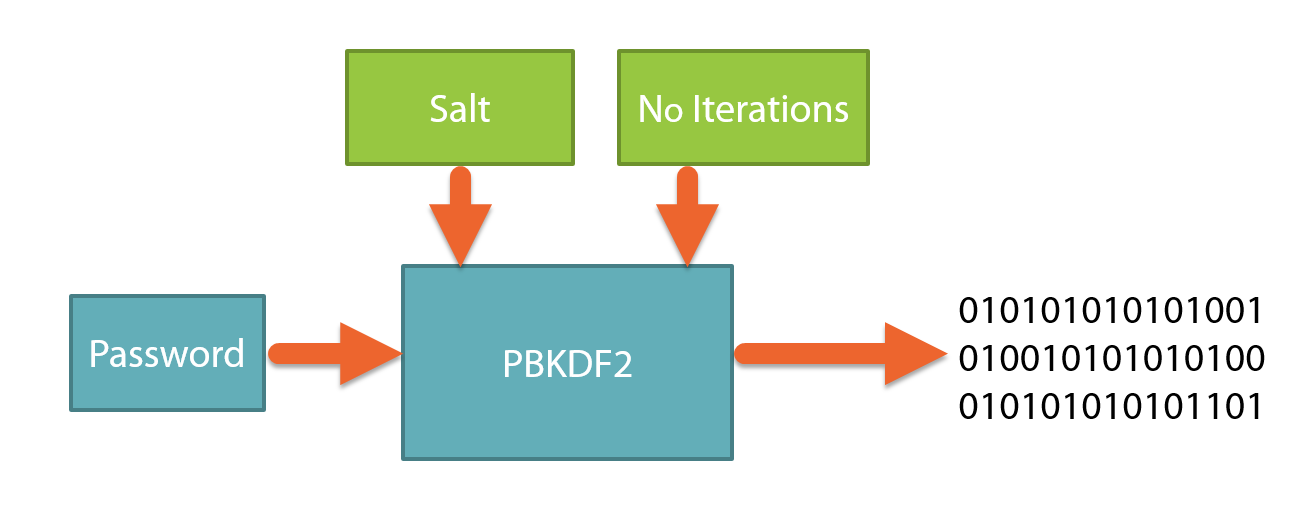
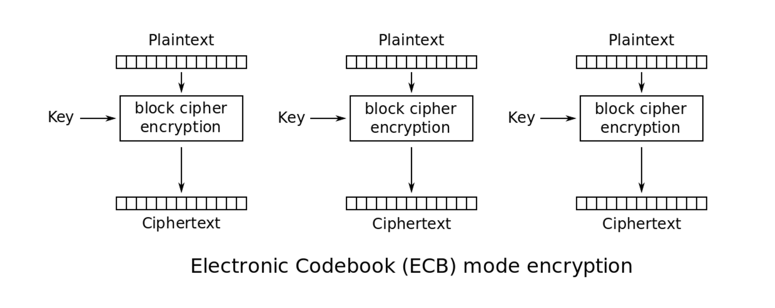
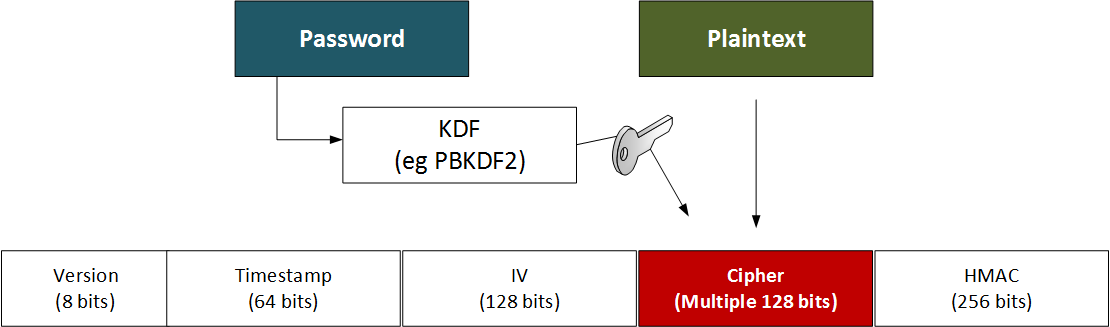
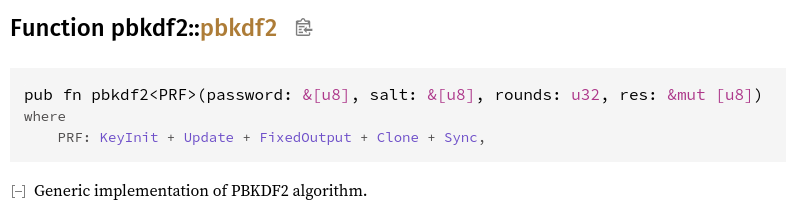
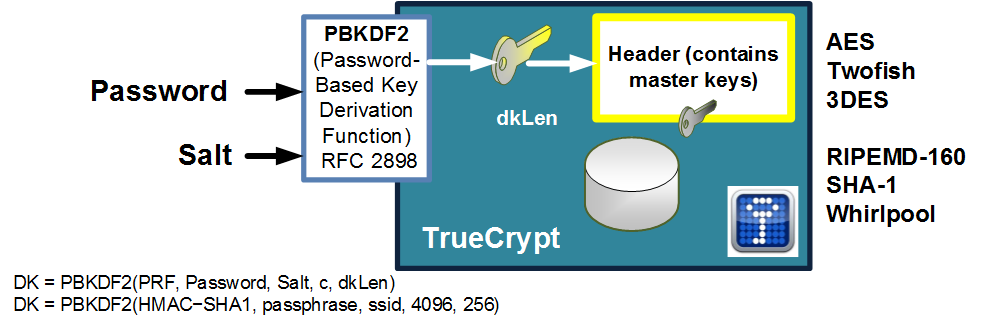
java - Encryption and Decryption with PBKDF2 and AES256 - practical example needed - how do I get the Derived key - Stack Overflow
How to keep passwords safe using PBKDF2 hashing algorithm in Java | by Oleksandr Stefanovskyi | Medium

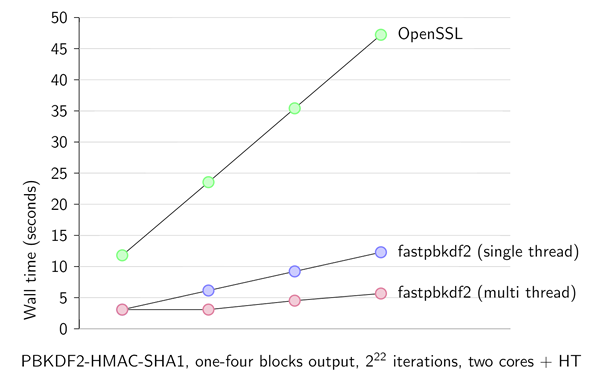
key generation - How exactly is the output of the XOR step in PBKDF2 used? - Cryptography Stack Exchange

Figure 1 from Energy-Efficient Hardware Implementation of LUKS PBKDF2 with AES on FPGA | Semantic Scholar